Global adaptation readiness and income mitigate sectoral climate change vulnerabilities | Humanities and Social Sciences Communications

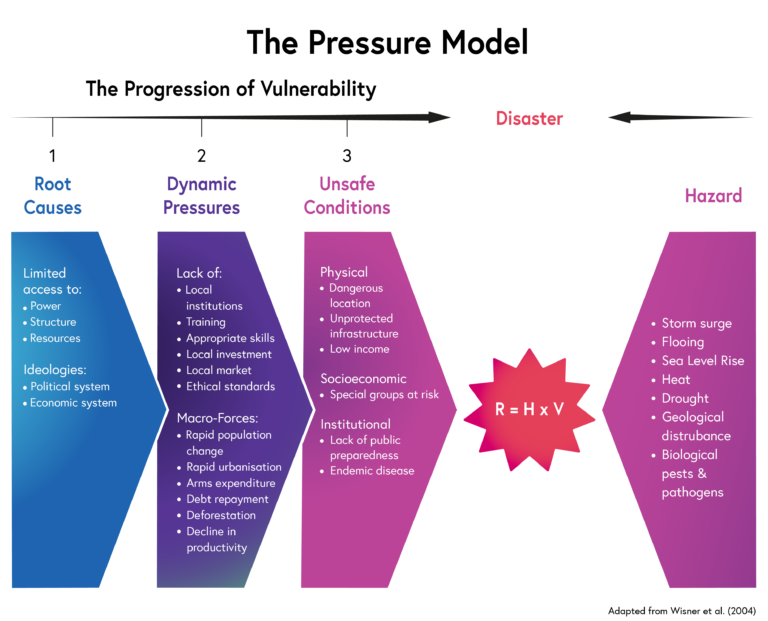
The four key drivers of vulnerability and the types of characteristics... | Download Scientific Diagram

Frontiers | Poverty Vulnerability and Health Risk Action Path of Families of Rural Elderly With Chronic Diseases: Empirical Analysis of 1,852 Families in Central and Western China

:max_bytes(150000):strip_icc()/why-vulnerability-in-relationships-is-so-important-5193728_final1-6585e6cf34134d7790fc240d3a4268e3.png)